Email security is more important than ever, and one of the most effective ways to protect yourself and your organization is by being vigilant about identifying potential spam. The SLAM method is a simple yet powerful framework that helps you spot suspicious emails before they do any harm. SLAM stands for S-sender, L-links, A-attachments, and M-message—key elements to evaluate when reviewing an email to determine whether it’s legitimate or spam.
What is the SLAM Method?
The SLAM method provides a systematic way to analyze an incoming email. By focusing on four core aspects of the message, users can spot red flags that may indicate a spam or phishing attempt. Here’s a breakdown of each element:
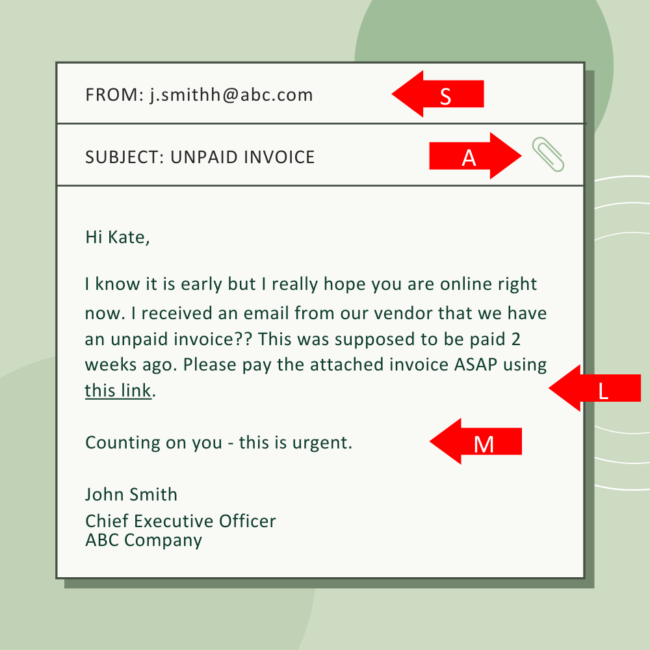
S – Sender
- Who is the email from?
Always start by scrutinizing the sender’s email address. Does it match the domain you expect? Be wary of slight misspellings or unusual characters in the sender’s address (e.g., “support@amaz0n.com” instead of “support@amazon.com“). - Is the sender trusted?
If you’re not familiar with the sender or the email seems to come from an unexpected source (like a company you’ve never interacted with), it’s a red flag. Official communications from reputable organizations typically use verified, consistent email addresses.
L – Links
- Hover before you click!
Links in spam emails often seem suspicious. Hover over any links in the email to see where they lead. If the URL doesn’t match the company’s official website or looks random (e.g., “clickhere999.com”), it’s a warning sign. - Don’t trust shortened URLs!
URL shortening services (like bit.ly) are commonly used in phishing scams to disguise the true destination of a link. If you see a shortened link, avoid clicking it unless you’re certain of the sender’s legitimacy.
A – Attachments
- Think before opening!
Be extremely cautious with email attachments, especially if they are unexpected. Spam emails often contain malicious files (e.g., .exe, .zip, .rar, .pdf) that can infect your system with malware. If you weren’t expecting an attachment or the file type seems unusual, don’t open it. - Check for double extensions!
Some malicious attachments may use double extensions to disguise themselves (e.g., “invoice.pdf.exe”). These files can be dangerous and should never be opened without verifying their authenticity.
M – Message
- Look for spelling and grammar mistakes.
Spam and phishing emails often contain poor grammar, awkward phrasing, and spelling errors. A legitimate organization will typically proofread its communications. If the email has odd formatting or seems off, proceed with caution. - Is the message urgent or threatening?
Be skeptical of emails that create a sense of urgency, like “Your account has been compromised—act immediately!” Legitimate companies generally don’t ask for sensitive information through email or pressure you to take immediate action. - Do they ask for personal information?
Authentic companies will never ask you to provide sensitive data such as passwords, social security numbers, or banking details via email. Any request for this type of information should raise immediate concerns.
How to Use the SLAM Method Effectively
- Stop. When you receive an unsolicited email, take a moment before acting. This pause will allow you to apply the SLAM method and evaluate the email carefully.
- Scan each component. Examine the sender, the links, the attachments, and the message for red flags.
- Verify. If anything seems suspicious, contact the supposed sender through a verified communication channel (not by replying to the email).
- Delete. When in doubt, delete the email. It’s always safer to ignore potential spam than to risk opening it.
By applying the SLAM method, you can significantly reduce your chances of falling victim to phishing, malware, and other types of email-based cyberattacks.