By Hugo Canedo
Scareware is a term used to describe deceptive software that aims to scare or trick users into taking actions that benefit malicious actors. These scareware programs often masquerade as legitimate security tools or alarming warnings, creating a sense of urgency and panic in users. However, with a little knowledge and caution, you can easily recognize and prevent scareware from causing any harm to your computer. In this beginner-friendly article, we’ll discuss what scareware is, how to recognize it, and how to protect yourself from falling victim to these deceptive tactics.
What is Scareware?
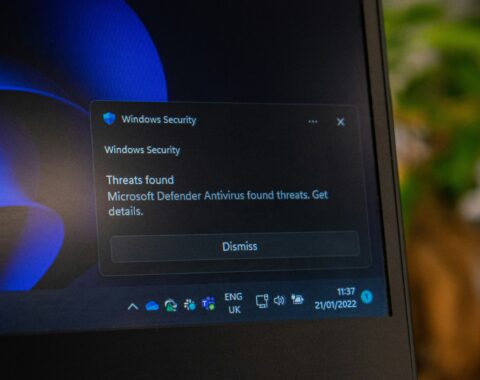
Scareware is a type of malicious software designed to exploit people’s fear and lack of knowledge about computer security. It typically comes in the form of pop-up messages, fake alerts, or advertisements that claim your computer is infected with malware, viruses, or other security threats. These warnings often look convincing, featuring official-sounding logos and jargon to make them appear legitimate.
How to Recognize Scareware
Recognizing scareware is crucial in preventing it from causing harm to your computer and personal information. Here are some tips to help you identify scareware:
- Urgency and Pressure: Scareware messages often use scare tactics, such as threatening data loss or system damage, and they insist you take immediate action. Legitimate security alerts don’t pressure you into hasty decisions.
- Spelling and Grammar: Poorly written messages or ones with numerous spelling and grammar mistakes are a red flag. Legitimate security warnings are typically well-crafted and professional.
- Unsolicited Pop-ups: Scareware usually appears as unsolicited pop-ups, especially on shady websites or in suspicious emails. Be cautious of any unexpected pop-up messages.
- Unknown Sources: If you’re not sure about the credibility of a security warning, research the source. Visit the official website of your antivirus or operating system to verify any alerts.
- Check Your Security Software: Don’t click on the pop-up messages or links within them. Instead, open your antivirus or security software and run a scan to check for real threats.
- Use Reputable Software: Only download and install security software from well-known, trusted sources. Avoid downloading security tools from pop-up ads or unfamiliar websites.

Preventing Scareware
Preventing scareware is a matter of staying informed and being cautious. Here’s how you can protect yourself from falling victim to scareware:
- Keep Your Software Updated: Ensure that your operating system, browser, and security software are up to date. Updates often include important security patches that protect against vulnerabilities.
- Use a Reputable Antivirus Program: Invest in a reliable antivirus program from a trusted provider. Regularly update and scan your system to catch and remove any real threats.
- Educate Yourself: Learn about common scareware tactics and how to recognize them. Share this knowledge with friends and family to help protect them too.
- Backup Your Data: Regularly back up your important data to an external drive or a cloud service. This way, you can restore your files in case of a malware attack.
- Be Cautious Online: Avoid visiting suspicious websites, clicking on random pop-ups, or downloading software from unverified sources. Stick to well-known websites and app stores.
- Enable Browser and Email Filters: Many web browsers and email providers have built-in filters to block known malicious websites and emails. Enable these filters for added protection.
- Check task manager for suspicious browser activity: By selecting ctrl+alt+del, you can view any odd browser behavior. Choose to end the task and the pop-up should disappear. Make sure to re-scan your system after a reboot.
Scareware can be alarming, but with some basic knowledge and vigilance, you can protect yourself and your computer from falling victim to these deceptive tactics. By recognizing the signs of scareware and following prevention tips, you’ll significantly reduce the risk of becoming a target. Stay informed, keep your software up to date, and trust your instincts when something seems too good to be true or too frightening to be real. Your computer’s security is in your hands, and by following these steps, you can keep it safe from scareware and other digital threats.
  |
Hugo Canedo is a Technical Support Specialist at Southridge Technology with a diverse background in System and Network Administration, Linux, and AWS Cloud support. He’s an avid participant in ethical hacking competitions, attends Defcon annually, and brings over 20 years of healthcare and military experience to his analytical and customer-oriented approach. Hugo is dedicated to staying current with technology trends and security projects. |
| Southridge Technology is a Connecticut based, whole-systems management IT service provider specializing in cyber-security and industry compliance; business continuity; WAN management, communications, and email hosting; cloud storage and backup solutions; and live, local, real-time monitoring and emergency response 24/7/365. We support organizations whose sizes range from one desktop to systems with over 400 endpoints. Our clients include both non-profit and private industries throughout the Northeast. |  |